In order to see SATA read and write performance in Linux you will need to follow the instructions below.
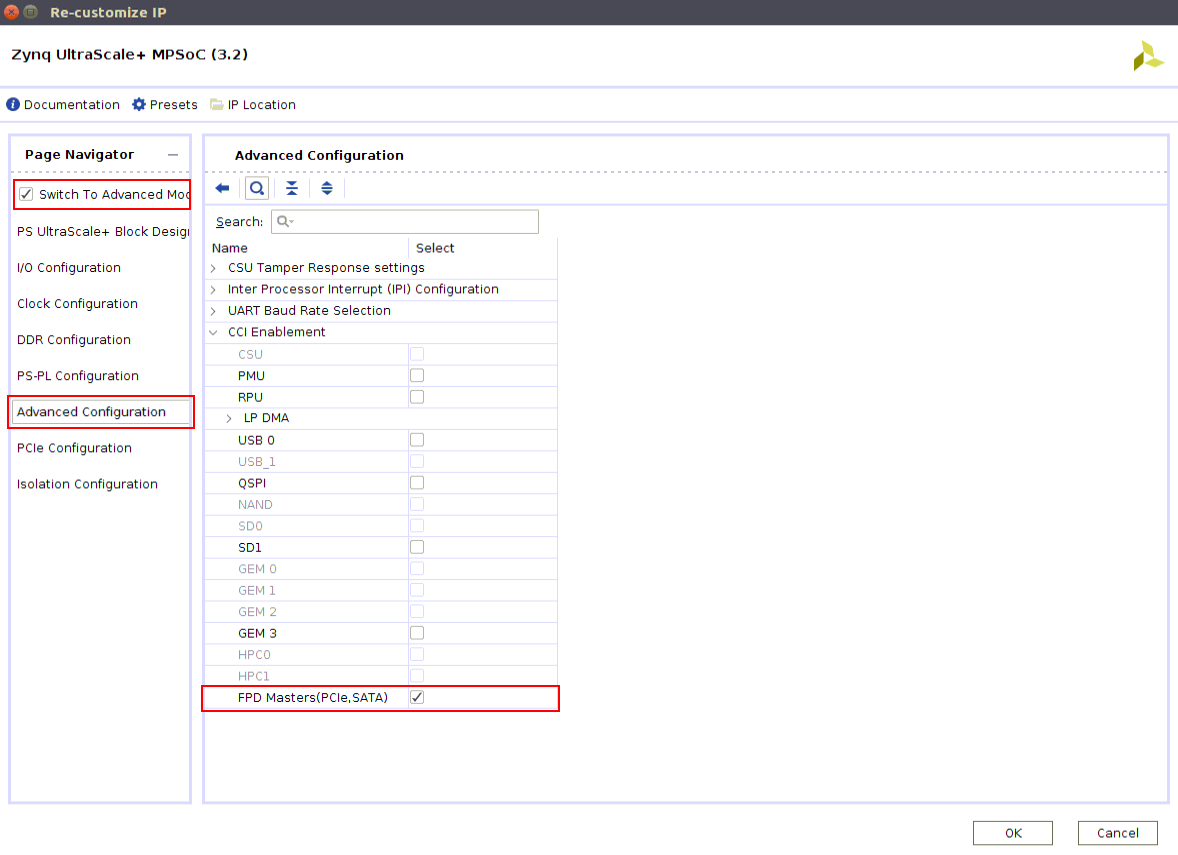
1) Enable CCI (Coherency) for the SATA controller in the Vivado design and generate the HDF as shown below:
2) Create a PetaLinux project using the above design HDF.
Refer to (UG1144) for more details.
3) Add the device-tree node for the SATA controller node in system-user.dtsi as shown below.
Note that you can apply the coherency to the SATA controller for each port.
unsigned long psu_apply_master_tz(void)
{
/*
* RPU
*/
/*
* DP TZ
*/
/*
* Register : slcr_dpdma @ 0XFD690040
* TrustZone classification for DisplayPort DMA
* PSU_FPD_SLCR_SECURE_SLCR_DPDMA_TZ 1
* DPDMA TrustZone Settings
* (OFFSET, MASK, VALUE) (0XFD690040, 0x00000001U ,0x00000001U)
*/
PSU_Mask_Write(FPD_SLCR_SECURE_SLCR_DPDMA_OFFSET,
0x00000001U, 0x00000001U);
/*##################################################################### */
/*
* SATA TZ
*/
/*
* Register : slcr_sata @ 0XFD690020 1
* SATA TrustZone Settings
* (OFFSET, MASK, VALUE) (0XFD690020, 0x0000000FU ,0x0000000FU)
*/
PSU_Mask_Write(0xFD690020, 0x0000000FU, 0x0000000FU);
/*
* PCIE TZ
*/
/*
* Register : slcr_pcie @ 0XFD690030
* TrustZone classification for DMA Channel 0
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_DMA_0 1
* TrustZone classification for DMA Channel 1
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_DMA_1 1
* TrustZone classification for DMA Channel 2
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_DMA_2 1
* TrustZone classification for DMA Channel 3
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_DMA_3 1
* TrustZone classification for Ingress Address Translation 0
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_0 1
* TrustZone classification for Ingress Address Translation 1
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_1 1
* TrustZone classification for Ingress Address Translation 2
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_2 1
* TrustZone classification for Ingress Address Translation 3
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_3 1
* TrustZone classification for Ingress Address Translation 4
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_4 1
* TrustZone classification for Ingress Address Translation 5
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_5 1
* TrustZone classification for Ingress Address Translation 6
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_6 1
* TrustZone classification for Ingress Address Translation 7
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_INGR_7 1
* TrustZone classification for Egress Address Translation 0
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_0 1
* TrustZone classification for Egress Address Translation 1
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_1 1
* TrustZone classification for Egress Address Translation 2
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_2 1
* TrustZone classification for Egress Address Translation 3
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_3 1
* TrustZone classification for Egress Address Translation 4
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_4 1
* TrustZone classification for Egress Address Translation 5
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_5 1
* TrustZone classification for Egress Address Translation 6
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_6 1
* TrustZone classification for Egress Address Translation 7
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_AT_EGR_7 1
* TrustZone classification for DMA Registers
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_DMA_REGS 1
* TrustZone classification for MSIx Table
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_MSIX_TABLE 1
* TrustZone classification for MSIx PBA
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_MSIX_PBA 1
* TrustZone classification for ECAM
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_ECAM 1
* TrustZone classification for Bridge Common Registers
* PSU_FPD_SLCR_SECURE_SLCR_PCIE_TZ_BRIDGE_REGS 1
* PCIe TrustZone settings. This register may only be modified during bootu
* p (while PCIe block is disabled)
* (OFFSET, MASK, VALUE) (0XFD690030, 0x01FFFFFFU ,0x01FFFFFFU)
*/
PSU_Mask_Write(FPD_SLCR_SECURE_SLCR_PCIE_OFFSET,
0x01FFFFFFU, 0x01FFFFFFU);
/*##################################################################### */
/*
* USB TZ
*/
/*
* Register : slcr_usb @ 0XFF4B0034
* TrustZone Classification for USB3_0
* PSU_LPD_SLCR_SECURE_SLCR_USB_TZ_USB3_0 1
* TrustZone Classification for USB3_1
* PSU_LPD_SLCR_SECURE_SLCR_USB_TZ_USB3_1 1
* USB3 TrustZone settings
* (OFFSET, MASK, VALUE) (0XFF4B0034, 0x00000003U ,0x00000003U)
*/
PSU_Mask_Write(LPD_SLCR_SECURE_SLCR_USB_OFFSET,
0x00000003U, 0x00000003U);
/*##################################################################### */
/*
* SD TZ
*/
/*
* Register : IOU_AXI_RPRTCN @ 0XFF240004
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_SD0_AXI_ARPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_SD1_AXI_ARPROT 2
* AXI read protection type selection
* (OFFSET, MASK, VALUE) (0XFF240004, 0x003F0000U ,0x00120000U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_RPRTCN_OFFSET,
0x003F0000U, 0x00120000U);
/*##################################################################### */
/*
* Register : IOU_AXI_WPRTCN @ 0XFF240000
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_SD0_AXI_AWPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_SD1_AXI_AWPROT 2
* AXI write protection type selection
* (OFFSET, MASK, VALUE) (0XFF240000, 0x003F0000U ,0x00120000U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_WPRTCN_OFFSET,
0x003F0000U, 0x00120000U);
/*##################################################################### */
/*
* GEM TZ
*/
/*
* Register : IOU_AXI_RPRTCN @ 0XFF240004
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_GEM0_AXI_ARPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_GEM1_AXI_ARPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_GEM2_AXI_ARPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_GEM3_AXI_ARPROT 2
* AXI read protection type selection
* (OFFSET, MASK, VALUE) (0XFF240004, 0x00000FFFU ,0x00000492U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_RPRTCN_OFFSET,
0x00000FFFU, 0x00000492U);
/*##################################################################### */
/*
* Register : IOU_AXI_WPRTCN @ 0XFF240000
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_GEM0_AXI_AWPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_GEM1_AXI_AWPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_GEM2_AXI_AWPROT 2
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_GEM3_AXI_AWPROT 2
* AXI write protection type selection
* (OFFSET, MASK, VALUE) (0XFF240000, 0x00000FFFU ,0x00000492U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_WPRTCN_OFFSET,
0x00000FFFU, 0x00000492U);
/*##################################################################### */
/*
* QSPI TZ
*/
/*
* Register : IOU_AXI_WPRTCN @ 0XFF240000
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_QSPI_AXI_AWPROT 2
* AXI write protection type selection
* (OFFSET, MASK, VALUE) (0XFF240000, 0x0E000000U ,0x04000000U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_WPRTCN_OFFSET,
0x0E000000U, 0x04000000U);
/*##################################################################### */
/*
* NAND TZ
*/
/*
* Register : IOU_AXI_RPRTCN @ 0XFF240004
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_RPRTCN_NAND_AXI_ARPROT 2
* AXI read protection type selection
* (OFFSET, MASK, VALUE) (0XFF240004, 0x01C00000U ,0x00800000U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_RPRTCN_OFFSET,
0x01C00000U, 0x00800000U);
/*##################################################################### */
/*
* Register : IOU_AXI_WPRTCN @ 0XFF240000
* AXI protection [0] = '0' : Normal access [0] = '1' : Previleged access [
* 1] = '0' : Secure access [1] = '1' : No secure access [2] = '0' : Data a
* ccess [2] = '1'' : Instruction access
* PSU_IOU_SECURE_SLCR_IOU_AXI_WPRTCN_NAND_AXI_AWPROT 2
* AXI write protection type selection
* (OFFSET, MASK, VALUE) (0XFF240000, 0x01C00000U ,0x00800000U)
*/
PSU_Mask_Write(IOU_SECURE_SLCR_IOU_AXI_WPRTCN_OFFSET,
0x01C00000U, 0x00800000U);
/*##################################################################### */
/*
* DMA TZ
*/
/*
* Register : slcr_adma @ 0XFF4B0024
* TrustZone Classification for ADMA
* PSU_LPD_SLCR_SECURE_SLCR_ADMA_TZ 0xFF
* RPU TrustZone settings
* (OFFSET, MASK, VALUE) (0XFF4B0024, 0x000000FFU ,0x000000FFU)
*/
PSU_Mask_Write(LPD_SLCR_SECURE_SLCR_ADMA_OFFSET,
0x000000FFU, 0x000000FFU);
/*##################################################################### */
/*
* Register : slcr_gdma @ 0XFD690050
* TrustZone Classification for GDMA
* PSU_FPD_SLCR_SECURE_SLCR_GDMA_TZ 0xFF
* GDMA Trustzone Settings
* (OFFSET, MASK, VALUE) (0XFD690050, 0x000000FFU ,0x000000FFU)
*/
PSU_Mask_Write(FPD_SLCR_SECURE_SLCR_GDMA_OFFSET,
0x000000FFU, 0x000000FFU);
/*##################################################################### */
return 1;
}